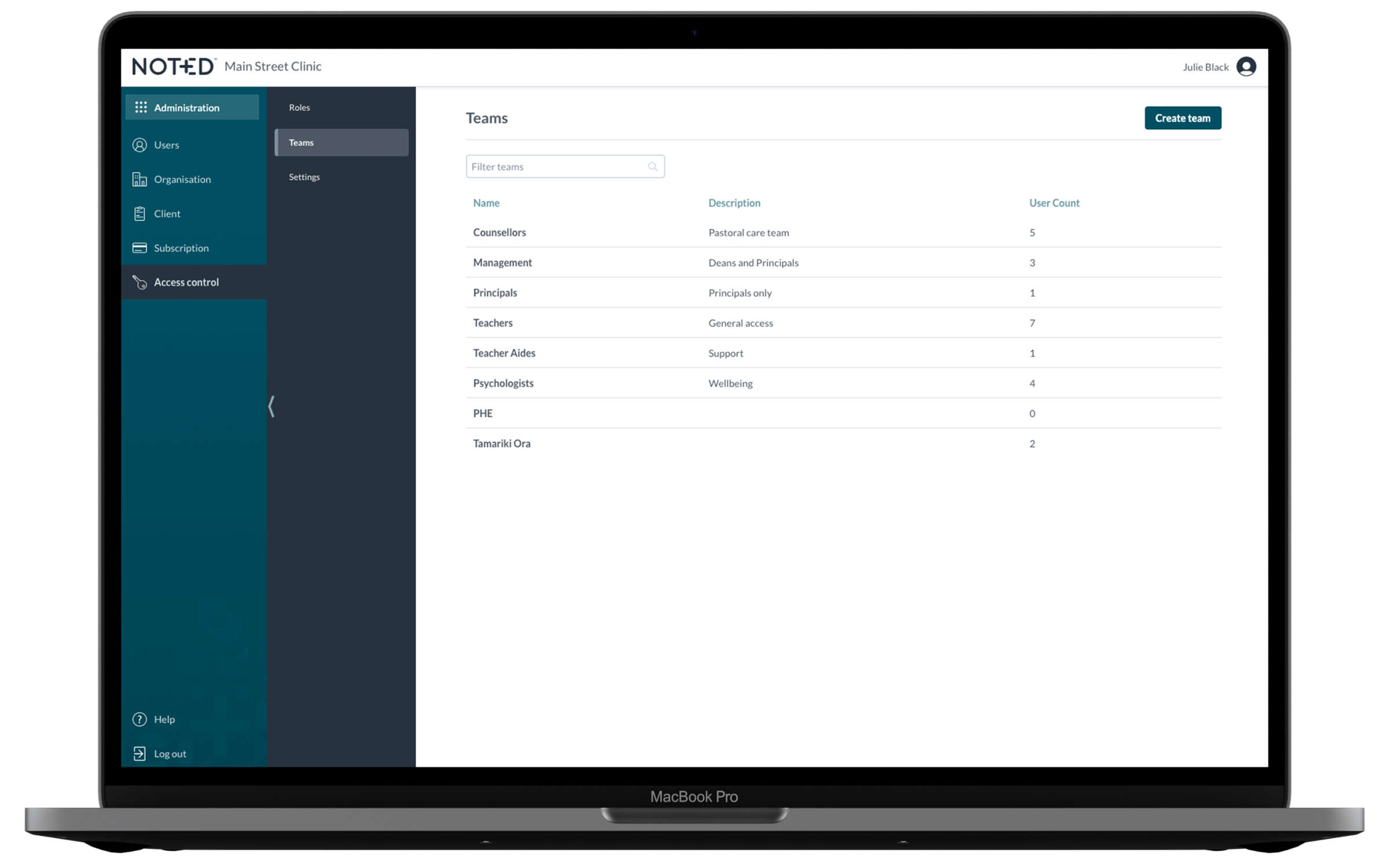
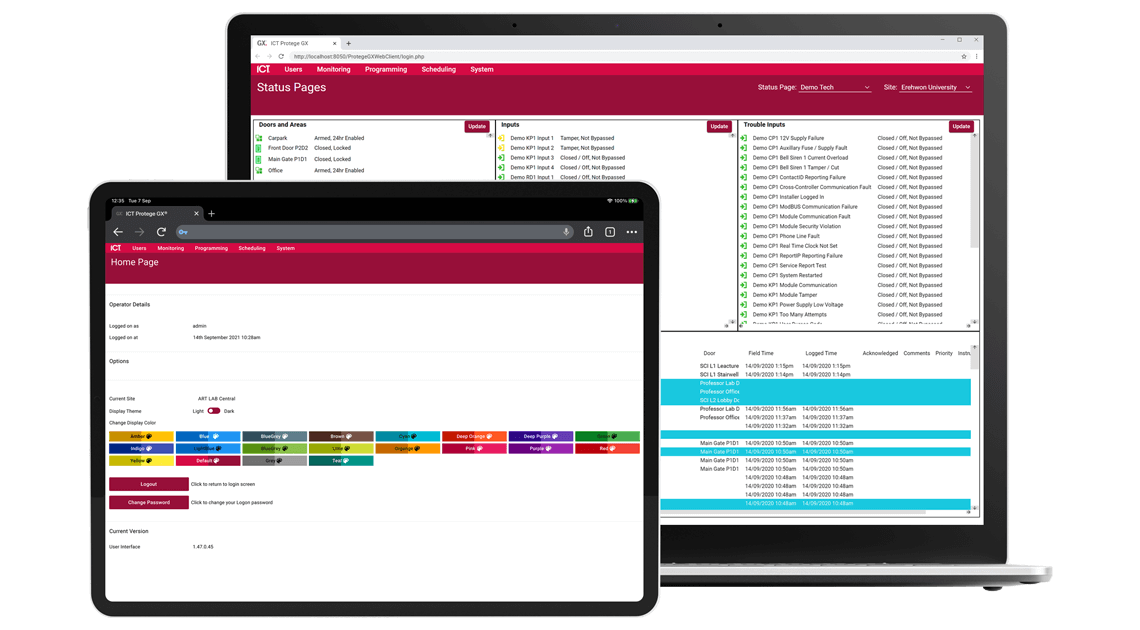
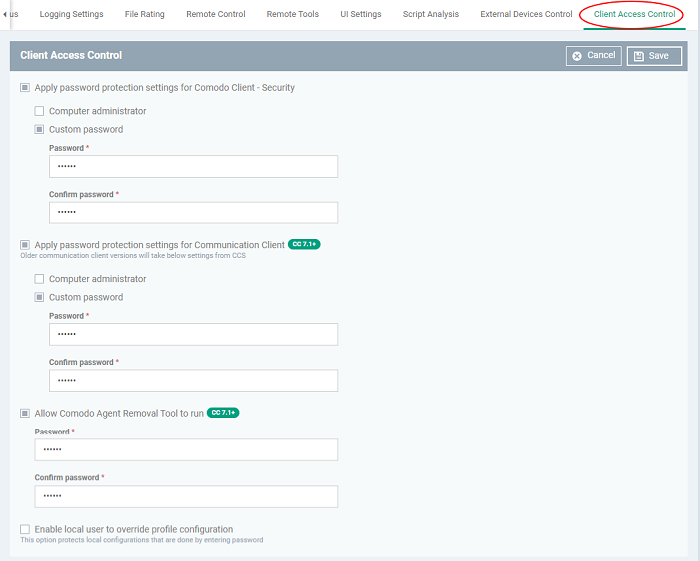
Security Guide - Edit Clients in the Client Access Control List (Enable the Client Access Control List)
Software House C•CURE 9000 Access control software Specifications | Software House Access control software
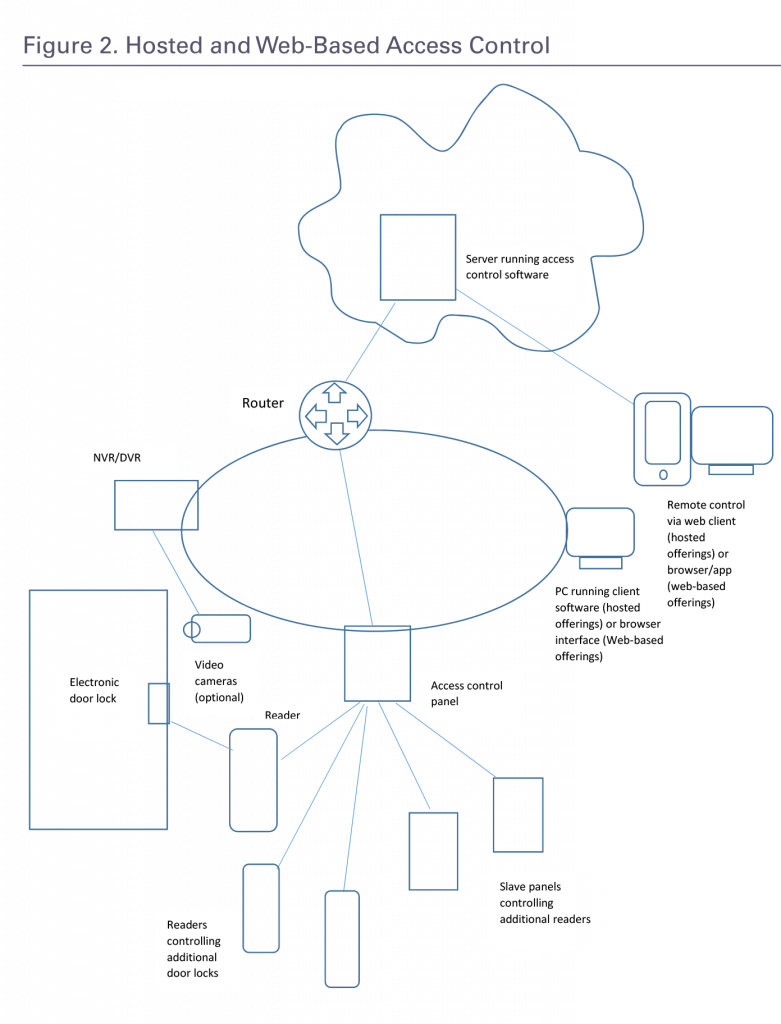
Cloud-Based and Hosted Access Control: Opportunities for Dealers and Integrators - Security Industry Association
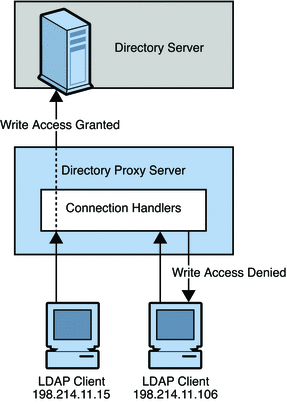
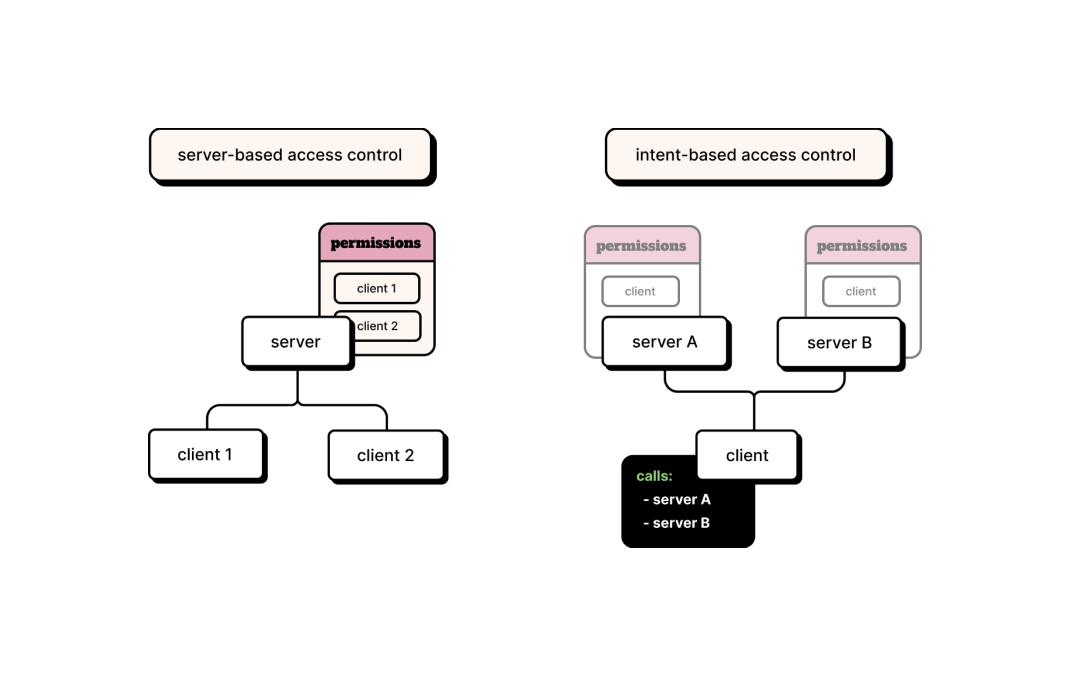
Designing Access Control With Directory Proxy Server (Sun Directory Server Enterprise Edition 7.0 Deployment Planning Guide)
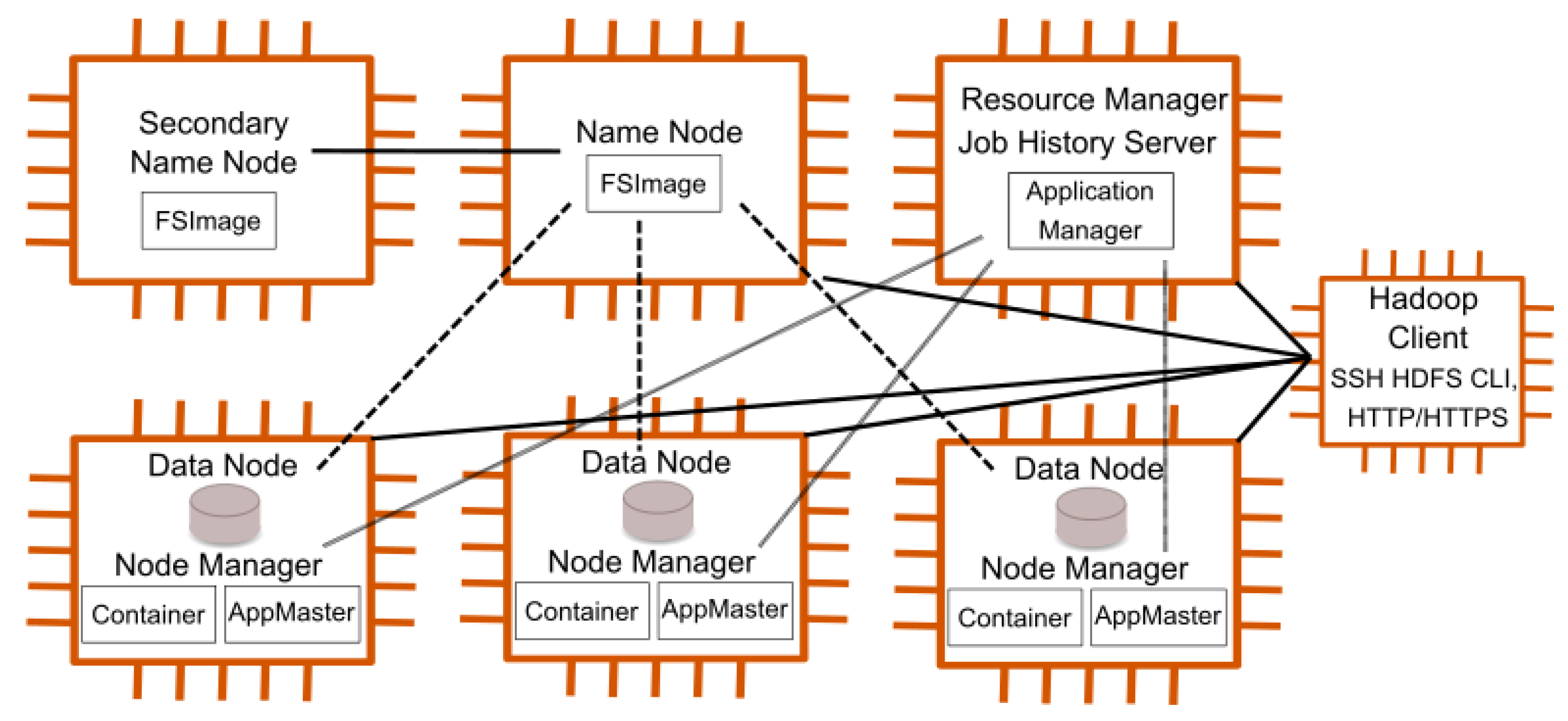



.png)