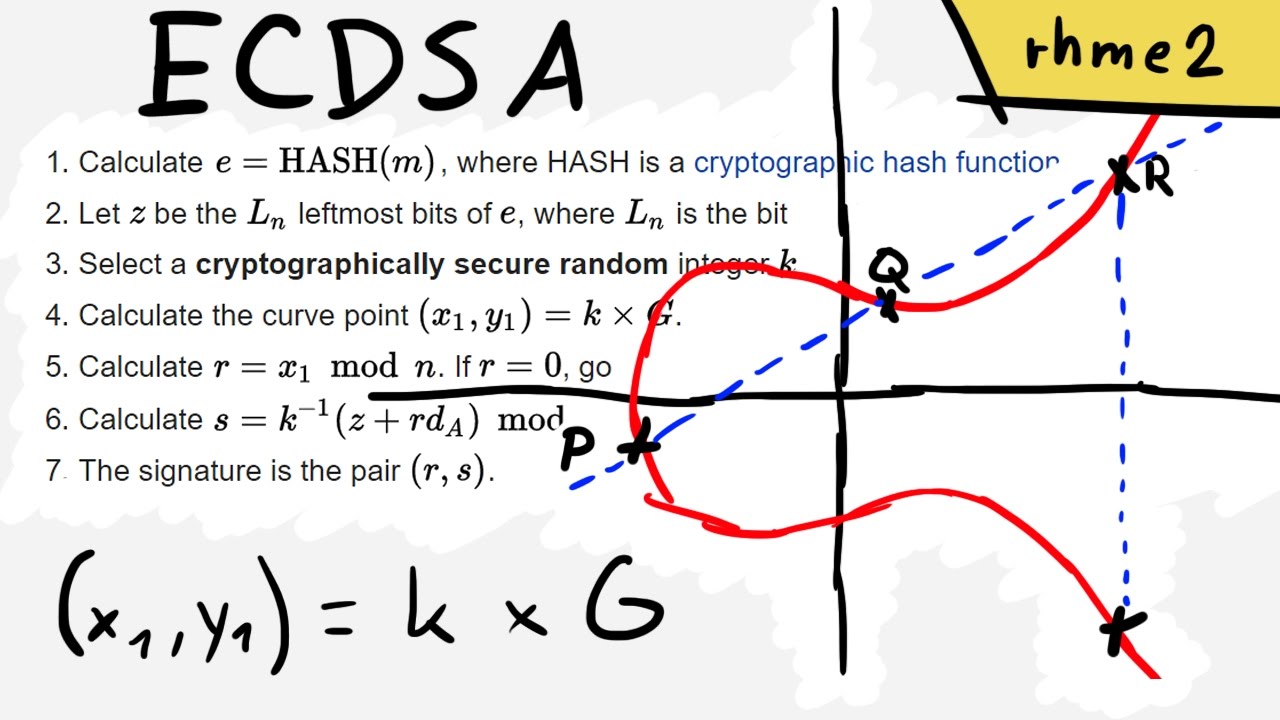
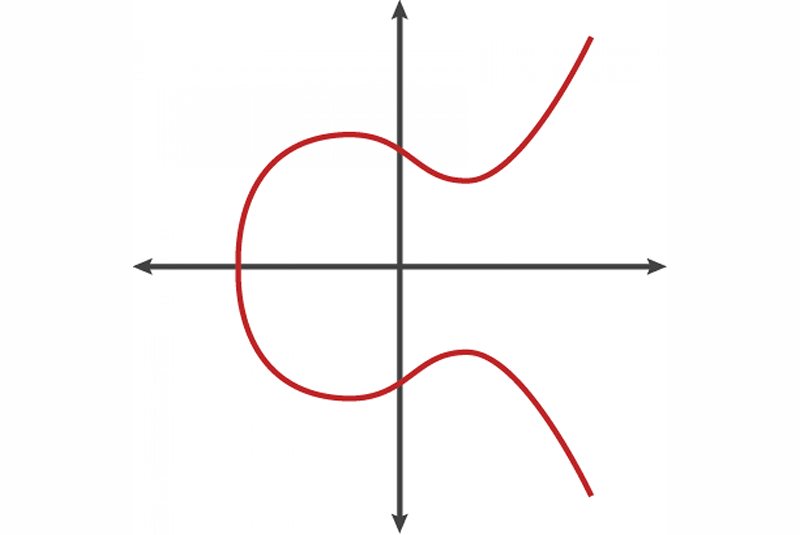
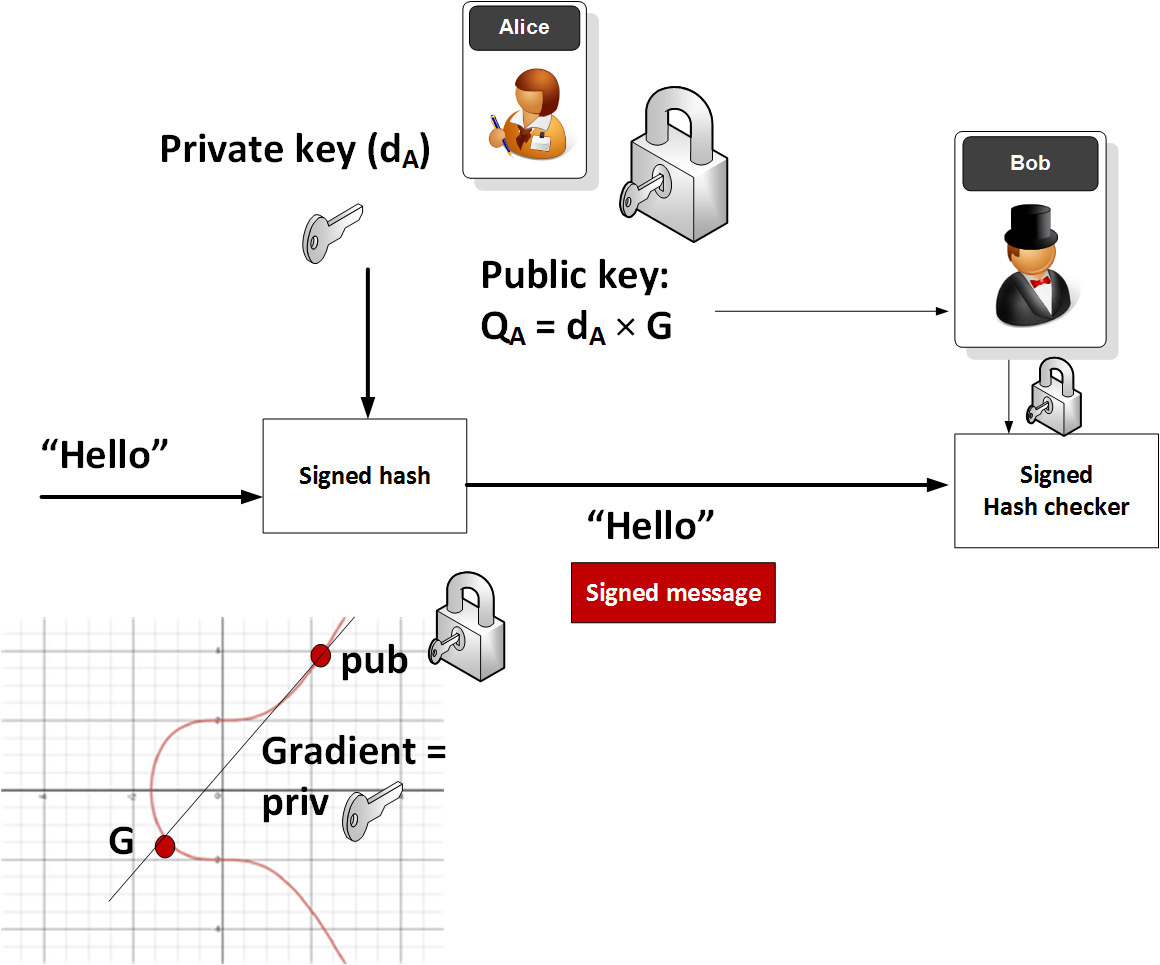
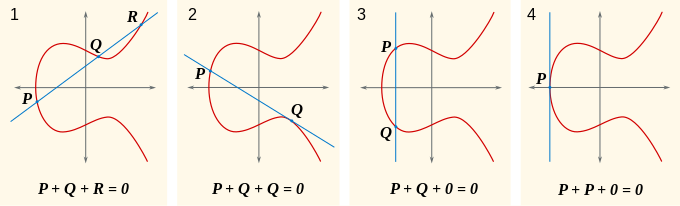
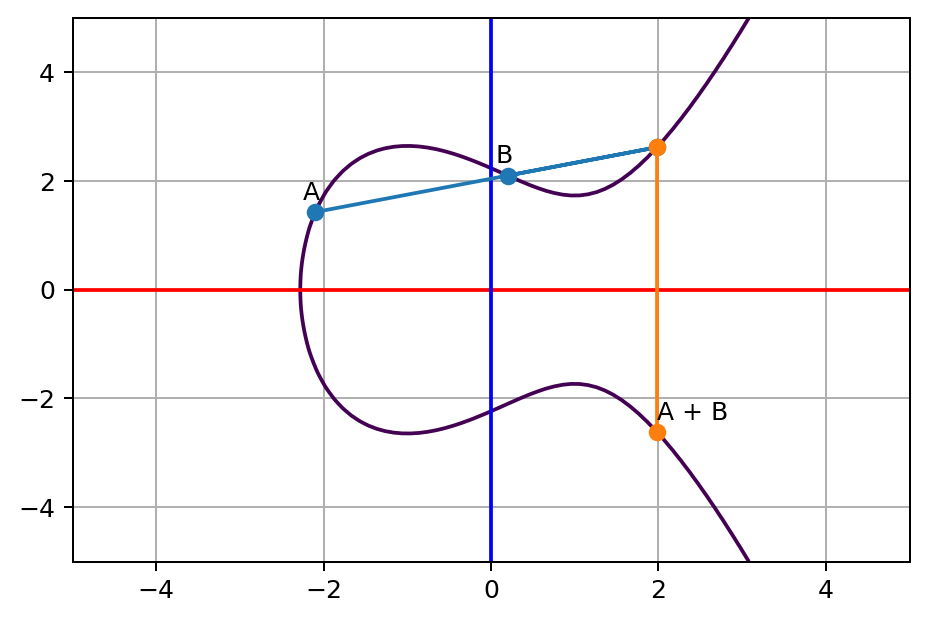
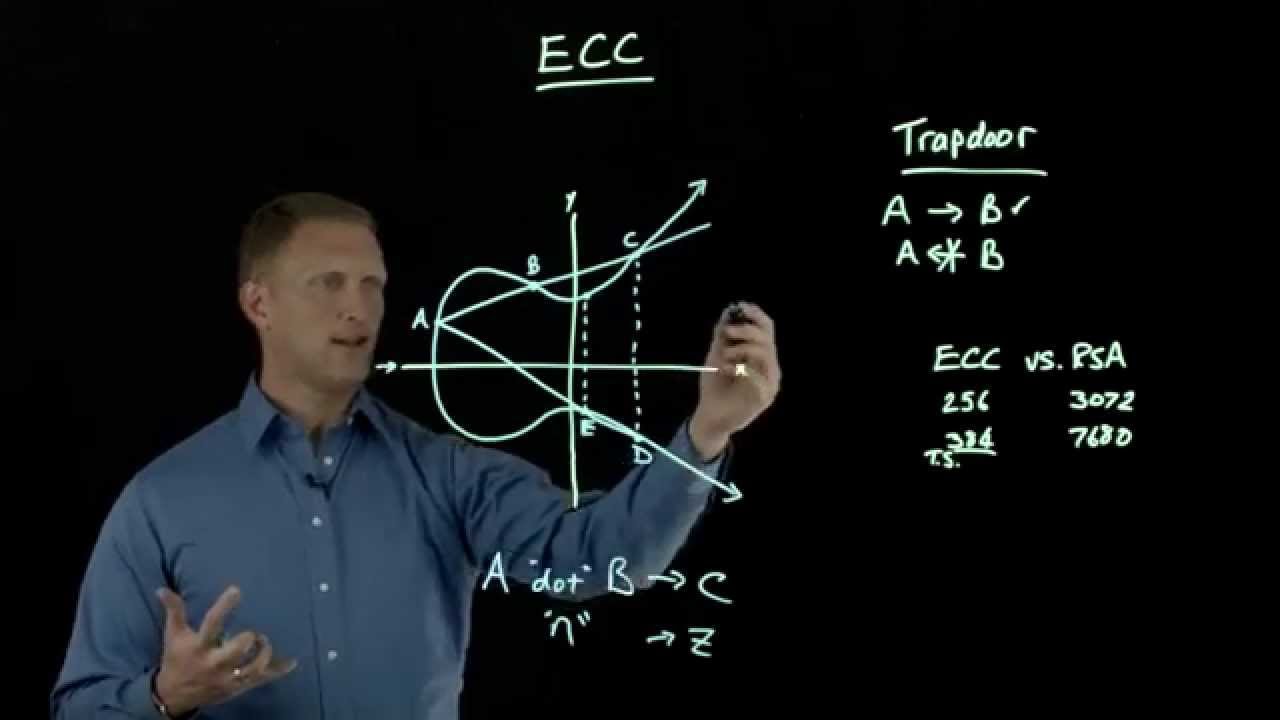
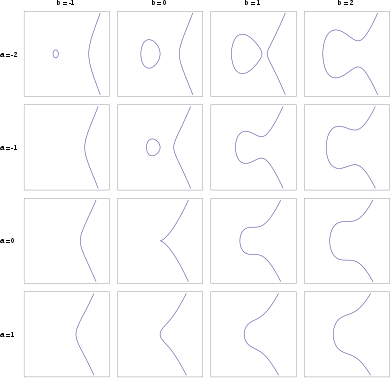
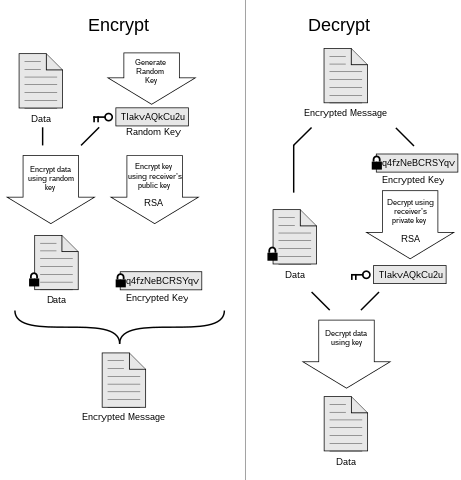
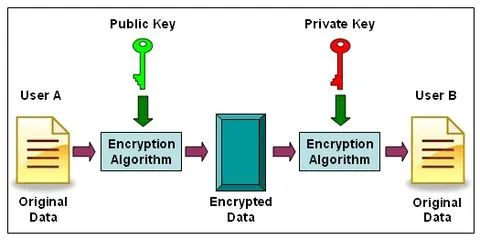
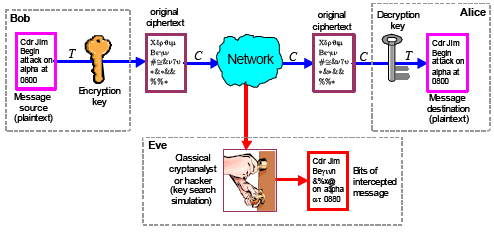
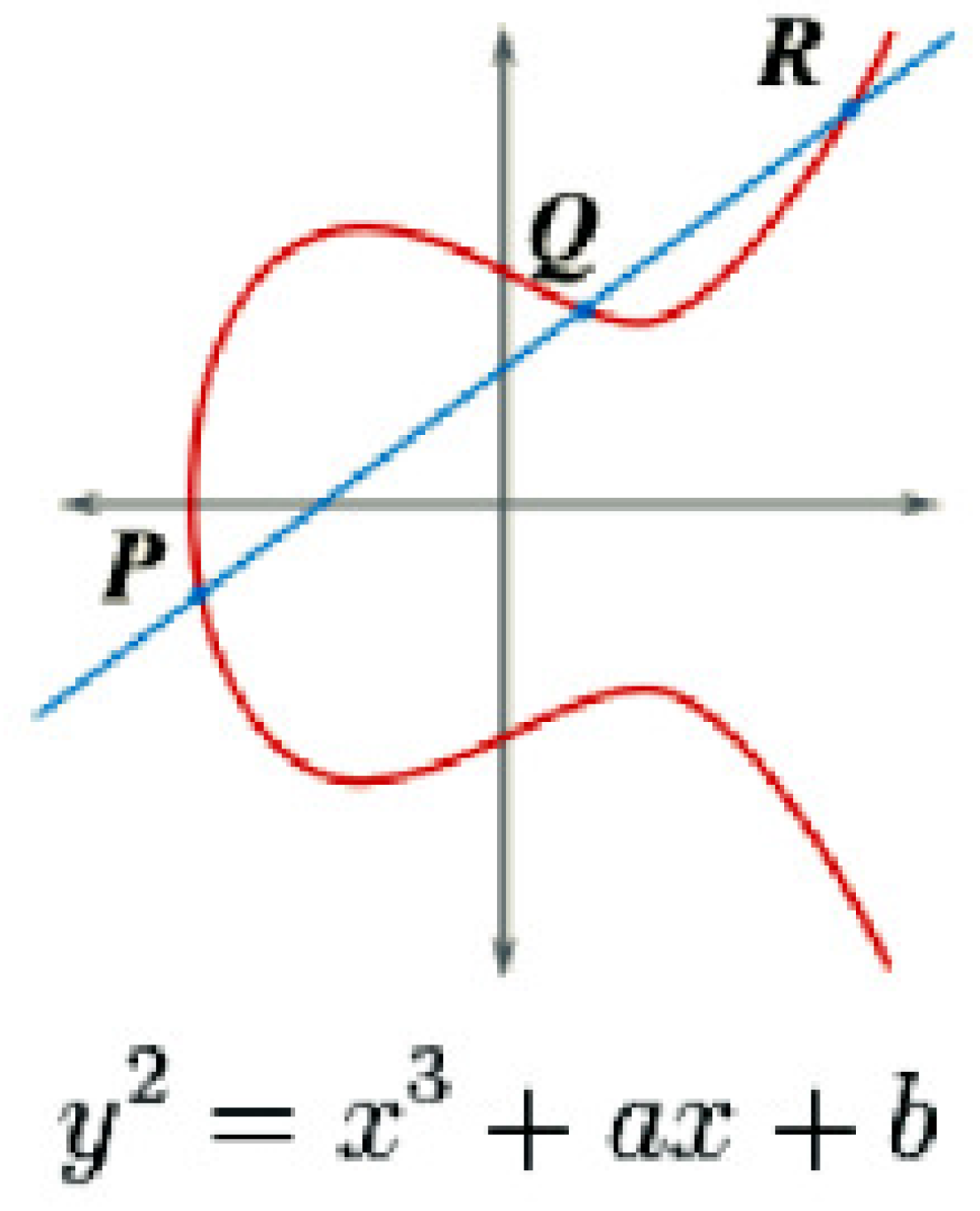
Cryptographic essence of Bitcoin: Part 2 — How do public/private keys work? Elliptical Cryptography & Proof of work | by Gayan Samarakoon | Medium
Cryptography | Free Full-Text | Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols
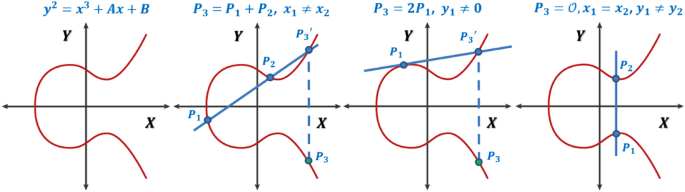
A generalized framework for elliptic curves based PRNG and its utilization in image encryption | Scientific Reports